SOC 2: A Strategic Security and Trust Framework for Modern Organizations

Introduction — Why SOC 2 Matters in a Data-Driven World
Today’s digital economy is defined by the relentless growth of cloud services, interconnected platforms, and real-time data exchange. At the same time, cyber threats continue to escalate in frequency and sophistication, with data breaches imposing substantial financial, legal, and reputational costs on organizations.
In this environment, traditional security postures — based solely on firewalls or endpoint protection — are insufficient. Customers, partners, and regulators increasingly demand demonstrable security assurance from the organizations they interact with. This demand has elevated voluntary security frameworks like SOC 2 from optional tech checkboxes to strategic business enablers.
SOC 2 provides a rigorous, third-party attestation model that enables organizations to validate their security controls, enhance trust, and mitigate data risk in a transparent, structured way.
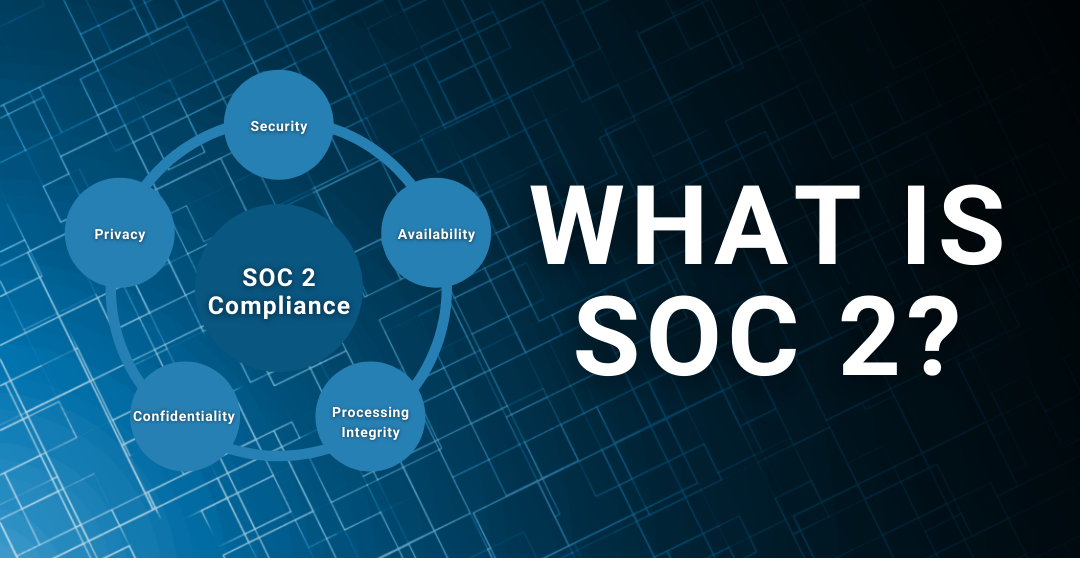
What Is SOC 2?
SOC 2 stands for System and Organization Controls 2, a security framework developed by the American Institute of Certified Public Accountants (AICPA) to evaluate how effectively organizations protect customer data.
Originally conceived as part of the SOC reporting suite, SOC 2 focuses specifically on security, privacy, and operational controls rather than on financial reporting (which is the focus of SOC 1). It is designed for service organizations — particularly those hosting, processing, or transmitting customer data in cloud-based environments — and assesses the maturity and effectiveness of internal controls through an independent audit.
Foundations and Trust Services Criteria
SOC 2 is grounded in the AICPA’s Trust Services Criteria (TSC), which define the core domains against which security and data-protection practices are measured. These criteria are:
- Security — Preventing unauthorized access, breaches, and system compromise.
- Availability — Ensuring systems and data are accessible when needed.
- Processing Integrity — Validating that data processing is complete, accurate, and timely.
- Confidentiality — Protecting sensitive information from unauthorized disclosure.
- Privacy — Safeguarding personal data in accordance with policy and legal obligations.
Security is treated as the baseline (Common Criteria) and is mandatory for all SOC 2 reports, while the other four criteria can be included based on business scope, customer requirements, and risk exposure.
What SOC 2 Compliance Means
SOC 2 compliance is not a legal requirement like GDPR or HIPAA, but rather a voluntary attestation framework with real market and contractual implications.
Complying with SOC 2 means that a licensed CPA or audit firm has independently evaluated an organization’s controls, policies, and evidence against the selected Trust Services Criteria and issued a SOC 2 report. This report provides assurance to customers, partners, and stakeholders that the organization has implemented appropriate controls to protect sensitive data.
There are two main SOC 2 report types:
- Type I: Assesses the design and implementation of controls at a specific point in time.
- Type II: Evaluates both the design and operating effectiveness of controls over a defined period (typically 3–12 months).
SOC 2 Type II reports are generally more valuable in high-trust or high-risk contexts because they demonstrate ongoing control effectiveness.
Why SOC 2 Is Useful for Corporations
Strengthening Security Posture
SOC 2 requires organizations to document, implement, and monitor specific controls — including access management, encryption, monitoring, incident response, and policy governance — that address real-world threats. This structured approach enhances an organization’s security maturity and operational resilience.
Building Customer and Partner Trust
For customers and enterprise buyers, a SOC 2 report is often considered a prerequisite for vendor selection. It demonstrates that a service provider has been independently assessed and that its security practices meet established criteria, thereby reducing perceived risk in procurement and due-diligence processes.
Facilitating Business Growth and Revenue
Many commercial contracts — especially in SaaS, fintech, and B2B services — explicitly require SOC 2 compliance. Achieving and publicizing SOC 2 status can accelerate sales cycles, unlock larger deals, and differentiate a company from competitors lacking such attestation.
Supporting Regulatory and Contractual Alignment
Although SOC 2 itself is not a regulation, its controls often map effectively to regulatory requirements such as GDPR, CCPA, and industry-specific obligations. This overlap reduces duplication in control implementation and supports broader compliance programs.

Using SOC 2 in Practice
Step 1: Scoping and Trust Services Criteria Selection
Organizations begin by defining the scope of their SOC 2 audit, identifying the systems, services, and data flows that will be evaluated. They also determine which Trust Services Criteria are relevant based on business context and stakeholder expectations.
Step 2: Control Implementation and Documentation
Once scoped, the organization implements policies, procedures, and technical controls to meet the selected criteria. Documentation and evidence collection are critical at this stage, as auditors will require verifiable artifacts during the audit process.
Step 3: External Audit and Attestation
An independent CPA audits the organization’s controls, measuring them against the Trust Services Criteria. The resulting SOC 2 report outlines findings, observations, and attestations regarding the design and effectiveness of those controls.
Step 4: Ongoing Monitoring and Improvement
SOC 2 compliance is continuous: organizations should monitor controls, address gaps identified in audits, and prepare for future assessments. This continuous loop supports both operational security and stakeholder confidence.
Benefits of SOC 2 Compliance
- Enhanced cybersecurity posture and reduced breach risk
- Greater confidence from customers, partners, and investors
- Reduced friction in commercial negotiations and procurement
- Stronger alignment with regulatory expectations and data-protection objectives
- Formalized governance and control documentation
Collectively, these benefits elevate the organization’s security credibility and prepare it for future regulatory or industry scrutiny.
SOC 2 Compared to Other Frameworks
Unlike prescriptive regulatory standards (e.g., HIPAA or PCI DSS), SOC 2 is criteria-based and flexible, allowing organizations to tailor their controls to their business model and risk profile. It is complementary to standards like ISO 27001, meaning organizations can pursue both in parallel to support broad enterprise risk and compliance programs.
Conclusion — SOC 2 as a Strategic Assurance Framework
SOC 2 has evolved from a niche compliance requirement into a strategic framework for governance, risk management, and operational security. In an era of persistent cyber threats and heightened customer expectations, SOC 2 provides a practical way for organizations to demonstrate control effectiveness, mitigate risk, and support growth.
Whether your company is a cloud service provider, a SaaS platform, or a financial institution handling sensitive data, SOC 2 compliance supports resilience, trust, and competitive differentiation. As threats evolve and security expectations rise, SOC 2 remains a core building block of modern cybersecurity assurance.



