ISO/IEC 27001: A Comprehensive Cybersecurity and Information Security Management Standard

Introduction — The Strategic Imperative of Information Security
In today’s digital economy, information is a core business asset. Organizations routinely process sensitive corporate data, customer information, intellectual property, and strategic plans across interconnected systems. At the same time, cyber threats have increased in sophistication, scale, and frequency, exposing companies to financial loss, reputational damage, and regulatory scrutiny.
To mitigate these risks and demonstrate robust information security practices, many organizations adopt internationally recognized frameworks. Among these, ISO/IEC 27001 stands out as the leading standard for establishing, implementing, maintaining, and continually improving an Information Security Management System (ISMS). It provides a systematic, risk-based approach to protect information assets against confidentiality, integrity, and availability threats.
What Is ISO/IEC 27001?
ISO/IEC 27001 is an international standard published by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC). It defines the requirements for an Information Security Management System (ISMS) — a structured set of policies, processes, technical controls, and governance mechanisms designed to manage and reduce information security risks.
Unlike prescriptive checklists, ISO 27001 is risk-based and scalable. It can be applied to organizations of all sizes and sectors. The standard requires organizations to justify controls based on their risk context, establish measurable objectives, and commit to continual improvement through the Plan-Do-Check-Act (PDCA) cycle.
Foundations and Key Components
ISO 27001 is structured around a few foundational elements:
- Leadership and Governance: Top management must demonstrate commitment and accountability for information security.
- Risk Assessment and Treatment: Organizations identify information security risks and select appropriate controls to mitigate them.
- Statement of Applicability (SoA): A documented declaration of which security controls have been selected, why, and how they are applied.
- Performance Evaluation: Internal audits, metrics, and management reviews assess how effectively the ISMS operates.
- Continuous Improvement: Corrective actions and periodic reassessments ensure the ISMS evolves with the threat landscape and business context.
While ISO 27001 defines what must be accomplished, it references a companion guidance document — ISO/IEC 27002 — which offers detailed best practices for controls such as access management, cryptography, incident response, and asset classification.
Why ISO/IEC 27001 Is Useful for Corporations
A Framework That Scales Across Industries
ISO 27001’s risk-based structure makes it relevant to organizations regardless of size or sector. Whether in finance, healthcare, technology, or manufacturing, the standard enables entities to tailor their ISMS to specific threats, business models, and regulatory environments.
International Recognition and Business Credibility
ISO standards are globally recognized. An ISO 27001 certification signals to customers, partners, and regulators that an organization has implemented a rigorous and independently audited information security management system. This credibility can facilitate international business, supply chain relationships, and cross-border data processing agreements.
Support for Regulatory Compliance
While ISO 27001 itself is not a legal requirement, its controls and processes align with many regulatory regimes. Adopting ISO 27001 often supports compliance with frameworks such as GDPR, PCI DSS, HIPAA, and NIS2, reducing duplication of effort and reinforcing broader risk and compliance programs.
Enterprise-Level Information Security Governance
ISO 27001 places a strong emphasis on leadership engagement, accountability, performance measurement, and governance. This elevates information security from a technical discipline to a strategic business function, improving risk visibility at the board and executive levels.
Implementing ISO/IEC 27001 in Practice
Step 1: Establish Scope and Leadership Commitment
Successful ISO 27001 implementation begins with defining the scope of the ISMS, identifying the information assets to protect, and securing formal commitment from top management to provide resources, governance, and oversight.
Step 2: Conduct a Risk Assessment
Organizations identify internal and external threats, vulnerabilities, and impacts to information assets. A documented risk assessment methodology forms the basis for selecting appropriate controls to mitigate identified risks.
Step 3: Select and Implement Controls
Based on the risk assessment, controls are selected from ISO 27001 and, where applicable, other frameworks. These may address access control, encryption, monitoring, incident response, physical security, or vendor risk.
Step 4: Performance Monitoring and Internal Audit
An internal audit program, supported by key performance indicators (KPIs), evaluates control effectiveness, identifies non-conformities, and informs corrective actions. Management reviews ensure that the ISMS continues to meet business needs.
Step 5: Certification Audit
While voluntary, many organizations pursue third-party certification. Independent certification audits evaluate whether the ISMS conforms to ISO 27001 requirements and operates effectively over time.
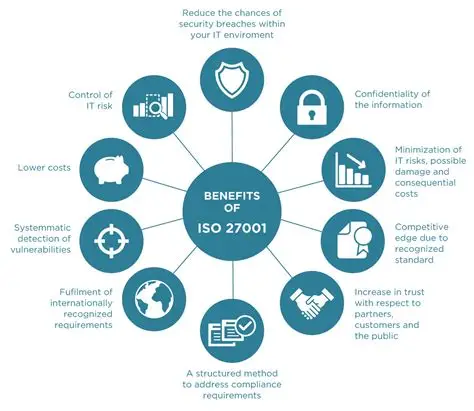
Key Benefits of ISO/IEC 27001 Adoption
- Risk-based protection of sensitive information across the organization.
- Improved governance, accountability, and executive visibility into information risk.
- Enhanced customer and partner trust through independent certification.
- Reinforced alignment with legal and regulatory obligations.
- Better integration with enterprise risk management (ERM) and compliance programs.
By embedding security into business processes and leadership structures, ISO 27001 strengthens an organization’s ability to anticipate, prevent, detect, and respond to cyber and information security challenges.
ISO 27001 and Other Frameworks
ISO 27001 is complementary to other security frameworks and standards. Organizations often pursue ISO 27001 alongside:
- SOC 2, to combine an ISMS with auditor attestation reports.
- NIST Cybersecurity Framework, for a detailed control taxonomy tied to governance.
- PCI DSS or HIPAA, for industry-specific regulatory compliance.
These frameworks can be mapped to ISO 27001 controls, enabling synergy across risk, compliance, and operational security functions.
Conclusion — ISO/IEC 27001 as a Strategic Security Foundation
ISO/IEC 27001 has become a cornerstone of enterprise information security, offering a systematic and internationally recognized way to protect information assets in a threat-rich environment.
By establishing a risk-based, governance-driven ISMS, organizations not only enhance their security posture but also reinforce trust with customers, partners, and regulators. Whether pursued as a compliance foundation, a confidence-building certification, or a strategic governance tool, ISO 27001 remains highly relevant for organizations seeking long-term resilience in an increasingly digital and interconnected world.



